This service provides planning and implementation to counter cyber threats to infrastructure and networks.
This service provides planning and implementation to counter cyber threats to infrastructure and networks.
Cyber security consulting is a service more specialized for infrastructure and networks, which implements measures to counter cyber threats and supports the maintenance of cyber security quality from the perspective of defense-in-depth including GW security*1 in the end-to-end communication from client devices to business software/applications. Of the PCI DSS*2 perspectives, this accounts for 80% of all cyber security measures.
Most attacks focusing on vulnerabilities generally start from the Internet, and that is why preventing external cyber threats before they occur is considered most important in GW security.
For example, when a vulnerability is discovered in a Web server, attacks that focus on that vulnerability can be detected and protected against before they occur using a WAF signature, which prevents those attacks from reaching the business software/applications. Patches then need to be applied to the business software/applications.
It is also desirable to link with cyber threat intelligence with a next-generation firewall before WAF is reached to block communication with malicious IP addresses, URLs, and domains in advance.
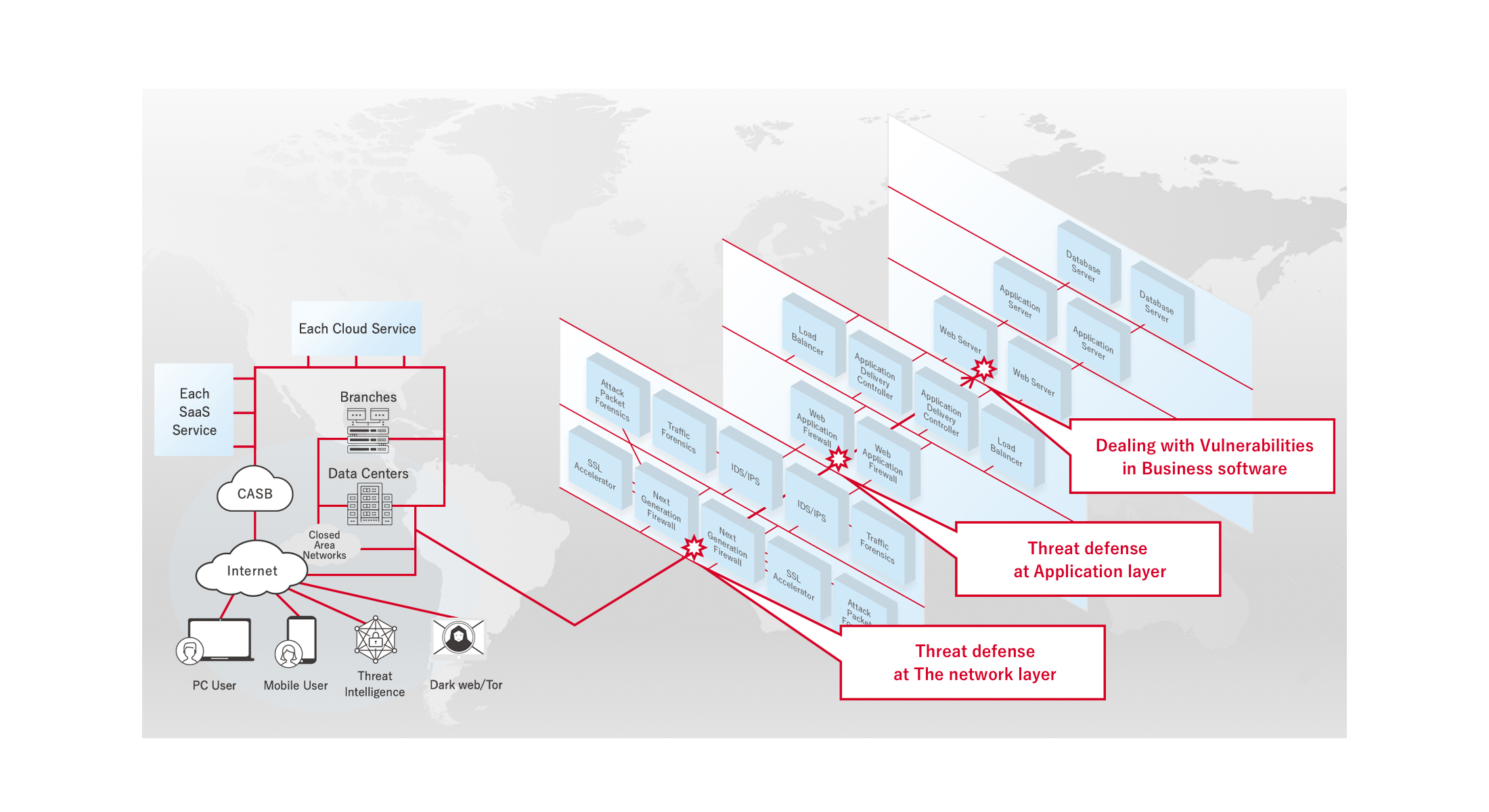
*1 : Definition of GW security
Client devices pass through many security gateways before they reach the business software/applications, such as a CASB, SSL Accelerator, Next-Generation Firewall, IDS/IPS, or WAF/ADC/LB. The most important thing is to detect and block malicious communication from outside in these security gateways that end-to-end communication passes through. It is also necessary to implement Endpoint Security (EDR) in client devices and servers in case an attack or infiltration still occurs.
*2 : Definition of PCI DSS
The PCI DSS (Payment Card Industry Data Security Standard) is an international standard for credit card information security jointly formulated by five international payment brands (American Express, Discover, JCB, MasterCard, and VISA).
Comprehensive support for improving the quality of cyber security
Our cyber security consulting service helps comprehensively improve the quality of cyber security in infrastructure across the entire network, including the Cloud, WANs, and LANs, and counters cyber threats to infrastructure and networks by handling everything from RFI/RFP in upstream phases to requirement definitions, the integration of operation, monitoring, and maintenance of CSIRT/SOC/MSSP/MDR, as well as the selection/evaluation of cyber security products such as firewalls and WAF, and basic/detailed design, validation, construction, and testing.






